CTI League in the Crossfire: Navigating Disinfo Campaigns Targeting Anti-Disinfo Efforts
(Clapping back at Matt Taibbi and Michael Shellenberger's bullshit)
Disinformation is a phenomenon which is not merely an Internet byproduct, but a weaponized form of information warfare.
Low on time? Listen to a 13m podcast discussion about this topic:
Disinfo involves the deliberate creation and dissemination of false or misleading information and is designed to deceive, manipulate public opinion, or obscure the truth. This issue has become a critical concern, particularly in the realms of politics, public health, and social discourse, where the impact of false information can have far-reaching consequences.
Cybersecurity professionals have emerged as crucial players in this landscape. Our role can transcend traditional notions of cybersecurity, which primarily focus on safeguarding systems and data from unauthorized access or attacks. In the context of disinfo, these professionals are increasingly recognized as frontline defenders, tasked with not only protecting information infrastructure but also ensuring the integrity of the information disseminated through these channels.

The expertise of cybersecurity professionals is multifaceted.
Cybersecurity encompasses skills in data analysis, which allows us to sift through vast amounts of online content to identify patterns and anomalies indicative of disinfo campaigns. Our proficiency in threat detection enables us to spot and neutralize attempts to infiltrate or compromise digital platforms, which are often used as conduits for spreading false information.
Additionally, our technical knowledge in digital forensics is crucial in tracing the origins and pathways of disinfo campaigns, which can be complex and multinational in scope.
From cybersecurity to cognitive security
Cognitive security, or “cogsec”, a nascent interdisciplinary field bridging cybersecurity and psychological principles, tackles the critical issue of how information shapes human thought and behavior, especially within the sphere of disinfo campaigns. Moving further beyond the conventional scope of cybersecurity, cogsec ventures into the domain of “information influence.” This involves a deep understanding of the ways in which inaccurate or deceptive information can sway individual perceptions, beliefs, and decision-making.
The emergence of cogsec and its intersectionality with cybersecurity signifies a transformative shift in handling information warfare and defense strategies, as traditional cybersecurity falls short in countering the targeting of algorithms and people to manipulate the lived reality of human beings and of their wider communities and nations.
Cogsec aims to bridge this gap by merging insights from psychology with cybersecurity methodologies.
The foundational concept here is that the human mind is susceptible to hacking via strategically crafted disinfo, influencing public opinion and societal norms. Thus, cogsec acknowledges that the protection of digital platforms is not just about technical measures but also about addressing the psychological impacts of the content shared on these platforms.
Cogsec practitioners examine the dynamics of information processing and assimilation among individuals and communities and how those processes can be skewed or manipulated. A key objective is to devise methods and tools for identifying and neutralizing efforts at cognitive manipulation, thus safeguarding individuals and societies from the detrimental impacts of disinfo.
This methodology recognizes that the primary targets of many cyber threats are not simply technological systems, but the very minds of their users. As such, there is an added emphasis on the importance of knowledge and awareness in protecting the public against disinfo. Those orchestrating such campaigns, known as influence actors, depend on a general lack of critical awareness to propagate and magnify their narratives.
Enhancing public comprehension of the mechanics and effects of disinfo can enable individuals to more critically assess the information they encounter. Such knowledge serves as a mental shield, diminishing the vulnerability of individuals to manipulation and deceit.
A growing market
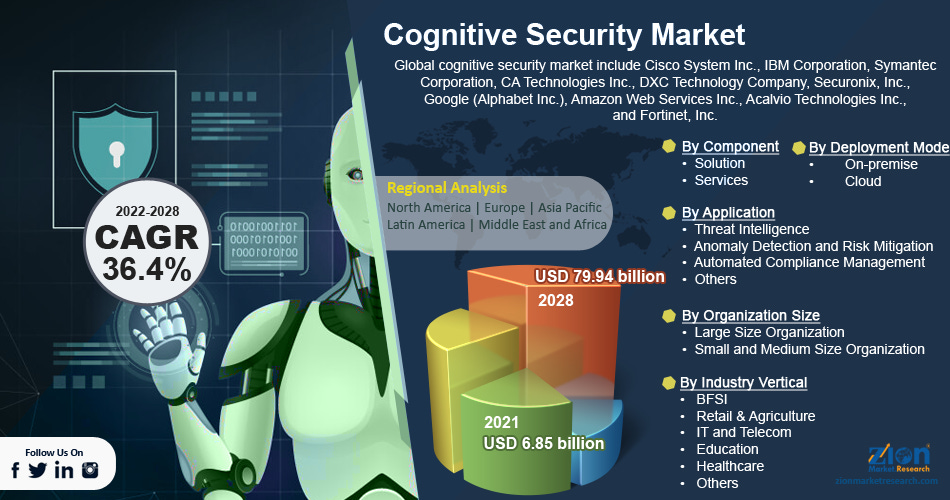
It is important to note that a burgeoning market is developing around technology solutions for cogsec, and several of the key players in that new and highly concentrated space are companies which are well-established in cybersecurity.
Industry publication CISO MAG predicted in a May 2018 article titled “Cognitive security to drive the future of infosec” that this market would grow to more than $3.85b in 2023. However, the most recent statistics for 2022 have blown that out of the water at $6.85b, and the market now encompasses an even wider set of applications and players.

Beyond the technology platforms powering this new market, the application of cogsec as a discipline strives to foster a more robust information ecosystem, where the public is shielded not only by digital security measures like firewalls, encryption, and new methods sourced from this emerging market, but also armed with the mental tools necessary to distinguish between truth and falsehood.
This comprehensive approach is vital in a time where information is both a key weapon and target. Technology, including AI, plays an important part in developing effective defensive strategies.
Therefore, professionals in these adjacent and interlocking fields are helping to serve as gatekeepers of digital integrity, a role which is increasingly vital in an era where information is routinely weaponized. By helping to maintain the veracity of online content, we can help uphold not just the security of data and systems, but also the sanctity of truth in public discourse.
This opportunity, however, is placing us in a vulnerable position.
Given our emerging role in combating disinfo, cybersecurity experts are increasingly finding ourselves targeted by the very elements we fight against. Influence campaigns, orchestrated by state or non-state actors, aim to discredit us and our work. Such campaigns are sophisticated and multifaceted, employing tactics like spreading false narratives, amplifying criticisms, and exploiting any factual or constructed vulnerabilities in the personal or professional lives of these experts.
The objective is clear: to sow doubt about the motives, methods, and findings of cybersecurity professionals, thereby undermining public trust in them.
Take the recent example of the Cyber Threat Intelligence League
From the perspective of credible sources such as Reuters and Wikipedia, the CTI League is recognized as a commendable, global volunteer initiative comprising cybersecurity experts, formed to combat heightened cyber threats during the COVID-19 pandemic. Focused primarily on protecting healthcare systems and critical infrastructure, the league has been instrumental in defending against a range of cyberattacks, including ransomware and phishing, particularly targeting medical facilities and frontline responders.
Lauded for its rapid formation in 2020 and significant impact, the CTI League has garnered attention for its collaborative approach, bringing together professionals from diverse backgrounds, including major companies like Microsoft and Amazon. The Leagues’s work, characterized by a blend of technical expertise and proactive defense strategies, has been crucial in safeguarding essential services during a critical time, earning recognition in the cybersecurity community and beyond for their voluntary, altruistic efforts in a global crisis.
However, to hear their work interpreted by journalistic hacks Matt Taibbi and Michael Shellenberger, the CTI League is a deeply sinister entity which is more than a volunteer cybersecurity force protecting healthcare systems and critical infrastructure during the COVID-19 pandemic. They say the League could be intricately involved in, or exploited by, a shadowy 'deep state' apparatus.
According to their narrative, the CTI League, potentially under the influence of undisclosed government entities, may have special access to ostensibly private data on these networks, and might be directly engaged in covert operations of censorship and disinformation. These insinuations paint the League as a possible pawn or participant in a broader, more nefarious scheme of control and manipulation, orchestrated by hidden forces within the U.S. government and potentially the Israeli government, as shown by their repeated targeting of, among other fellow industry professionals, CTI League co-founder Ohad Zaidenberg with vague insinuations. Their dark portrayal appears intended to raise grave concerns amongst the public about the League's role in a larger, dark agenda of information warfare, societal manipulation, and the undermining of democratic processes by unseen elements of the so-called “deep state.”
Except–it’s all bullshit.
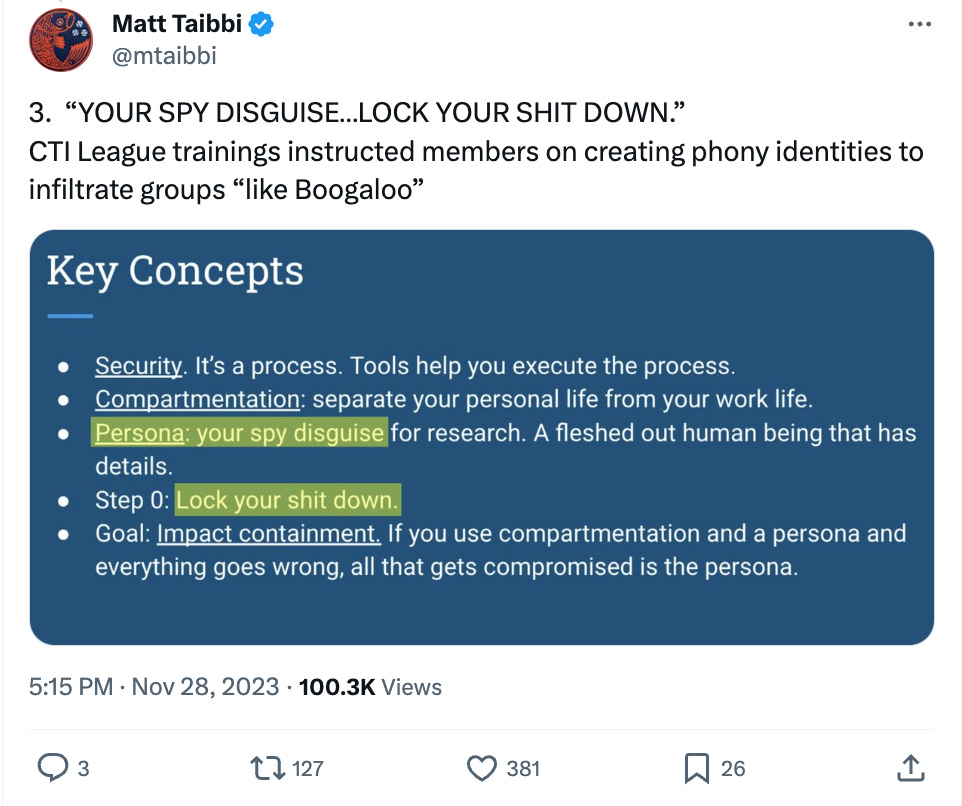
On November 28, 2023, Taibbi started tweeting multiple long threads full of slides supposedly leaked from the CTI League which contain nothing of note when reviewed by an expert, yet were seemingly prepared to generate maximum outrage from his and Shellenberger’s respective audiences.
For example:
Why would Taibbi take offense with volunteers infiltrating the Boogaloo, an extremist movement which incubates insurectionists and domestic terrorists?
Don’t we want help with that?
There is literally nothing here of note. The highlights in the threads mean nothing. The method in which these were presented was not journalistic. In fact, one could call it yellow journalism.
This is media which was made to frighten people with information which is divorced from its original, layered context, if it is even authentic at all.

Taibbi and Shellenberger have expanded their narrative to Substack, yet I was not able to identify a single claim that held water within context of the CTI League’s mission and common cybersecurity practices.
While the League has released a comprehensive statement which systematically and effectively refutes these allegations, as well as a separate statement from their well-respected founder, Marc Rogers, more people will have been reached by the initial influence campaign than can be effectively remedied now. The individuals targeted by this campaign are unlikely to be reached or swayed by verifiable facts after consuming this misrepresented content.
That’s the point.
Both statements present a coherent and consistent narrative about the CTI League's origins, objectives, and operations which aligns with previous press and my own research on their operations. They emphasize the altruistic and voluntary nature of the group, formed in response to a global crisis, and focus on protecting critical infrastructure.
The statements’ emphasis on collaboration with government agencies being limited and focused, along with the clarification of the volunteers' capabilities, counters the narrative of a covert censorship operation. The statements also highlight the importance of private and volunteer efforts in cybersecurity, especially in sectors like healthcare that are vulnerable to attacks.
Having been a Director of Incident Response at major security companies, I can personally attest to the importance of such partnerships, which are commonplace in the information security industry.
The detailed refutations of specific allegations, along with the willingness to release documents for public scrutiny (albeit redacted for safety), suggest a particular level of transparency and accountability which has not been forthcoming from the accusatory “journalists” whose sources remain anonymous and files remain unpublished despite their sensationalistic “#CTIFiles” hashtag.
Given all available information, including statements and evidence (or lack thereof) from those making allegations, and my own knowledge of the players and work involved, the insinuations of wrongdoing against the CTI League seem to be, at best, misfounded, and at worst, veering towards conspiracy theory territory, lacking any substantial evidence to support the more serious allegations of collusion with the government to repress information from Americans for political reasons.
Who are Taibbi and Shellenberger, and why are they pushing this narrative?
You may remember Matt Taibbi from the supposed “#TwitterFiles” scandal he tried to whip up in 2022, which MSNBC attributed to Elon Musk.

“Ultimately, that’s all that the author of the “Twitter Files,” conservative Substack writer Matt Taibbi, was able to report from the scores of documents he supposedly received from Twitter employees: that the company, which rightly faced blowback for allowing disinformation on its platform during the 2016 election, debated internally whether and how to prevent a story involving Hunter Biden from taking hold on the site in October 2020.
(Taibbi also seems to have revealed some personal email addresses after appearing to share the documents at Musk’s direction.)”
-J'a’Han Jones in MSNBC, Dec 5, 2022
As for Taibbi’s colleague Michael Shellenberger, the first page of his Google News results says a lot, doesn’t it?
In a recent live taping on The Hill, Shellenberger said that he spoke before the committee that oversees the Department of Homeland Security to provide the following perspective (all bolding and emphasis is mine):
“The question is what should be done about all this evidence of censorship by this particular agency, CISA.”
“I believe that given what it’s done, it should be abolished.”
–Michael Shellenberger, The Hill, Dec 14, 2023
This is clearly Shellenberger’s goal.
To turn the American public against the Cybersecurity and Infrastructure Security Agency (CISA), which performs vital functions within the U.S. Government and is an agency–in the opinion of the wider security community–which deserves an increasing annual budget to meet the current need. Not “abolishment”!
That’s absolute nuttery. Bad for America!
I also spotted several statements in direct contradiction with the CTI League’s statement. For example, the League stated they had no relationship or communication with Stanford.
Is Shellenberger perhaps operating with false information?
We don’t know who Taibbi and Shellenberger’s purported source or sources are, and we do not have the “files” themselves. No major media organization has seemingly been able to verify this information to run a story themselves.
Heritage Foundation’s Project 2025 “Presidential Transition Project” (fascist manifesto), a plan created by hundreds of influential insiders within the GOP to entirely remake the United States in a fascist image in the event of a Trump win in 2024 is very clear about its desire to abolish CISA, which itself has been a target of the GOP (the purported party of ‘law and order’) for quite some time.
One has ask themselves why.
The following excerpt from Project 2025 was authored by previously illegally-appointed DHS second-in-command (and, more recently, Ron DeSantis fanatic and sex trafficking obsessive) Ken Cuccinelli:
“Of the utmost urgency is immediately ending CISA’s counter-mis/disinformation efforts. The federal government cannot be the arbiter of truth. CISA began this work because of alleged Russian misinformation in the 2016 election, which in fact turned out to be a Clinton campaign “dirty trick.”
The Intelligence Community, including the NSA or DOD, should counter foreign actors. At the time of this writing, release of the Twitter Files has demonstrated that CISA has devolved into an unconstitutional censoring and election engineering apparatus of the political Left.
In any event, the entirety of the CISA Cybersecurity Advisory Committee should be dismissed on Day One.”
-Ken Cuccinelli in Heritage Foundation’s Project 2025
As we now know, Russian attempts to influence the 2016 election have been proven many times over, the sensational #TwitterFiles were a big ‘nothingburger’ discredited by the respectable press, and both Cuccinelli and Shellenberger want the cybersecurity apparatus of the federal government to be disbanded.
I hope you are able to spot the alignment within these narratives.
Disinfo about anti-disinfo efforts (!)
The phenomenon of “disinfo about anti-disinfo” involves the spread of false or misleading information specifically targeting initiatives designed to combat disinformation.
Here are some key aspects and considerations:
Undermining Credibility: These campaigns often aim to discredit organizations or individuals involved in identifying and countering disinfo. By casting doubt on their motives or methods, the campaigns can reduce public trust in these entities.
Confusion and Doubt: By generating false narratives about anti-disinfo efforts, such campaigns create a layer of confusion. This makes it harder for the public to distinguish between legitimate and illegitimate sources of information.
Political and Ideological Motives: Often, these disinfo campaigns are driven by political or ideological motives. Actors who benefit from the spread of disinfo may target anti-disinfo initiatives to continue their manipulative practices unchallenged.
Common tactics include:
False Allegations: Accusing anti-disinfo organizations or individuals of bias, hidden agendas, or even spreading disinformation themselves.
Conspiracy Theories: Propagating conspiracy theories that allege collusion between anti-disinfo groups and political entities, governments, or corporations.
Manipulation of Facts: Twisting or taking out of context the actions and statements of anti-disinfo groups to misrepresent their goals and methods.
DARVO: Deny Attack, Reverse Victim and Offender. This often manifests as accusations towards others of the behaviors which they themselves are engaged in.
Complexity of Claims: Complex disinfo attacks with many intersecting details are more cognitively difficult for individuals to process and affect the likelihood an attacker will be successful in influencing their target audience.
Challenges in countering this phenomenon include:
Complexity of Attribution: Determining the source of disinfo about anti-disinfo efforts can be challenging due to the use of anonymous or pseudonymous online identities and the involvement of state or non-state actors.
Rapid Spread on SM: The viral nature of social media platforms facilitates the rapid spread of disinfo, making it difficult to contain or correct false narratives once they gain traction.
Public Skepticism: In an era where trust in institutions is declining, disinfo campaigns can exploit and deepen public skepticism, making the work behind anti-disinfo initiatives all the more challenging.
They do it because it works
This strategy of targeting defenders of digital integrity is part of a broader tactic often used in information warfare: attacking the source to discredit the message.
By casting aspersions on the credibility and trustworthiness of cybersecurity experts, these campaigns attempt to weaken one of the primary frontline defenses against disinformation. This not only poses a risk to the individuals involved but also to the broader societal trust in digital platforms and the information ecosystem, ultimately negatively affecting the ties which bind us.
So, when you hear bullshit artists like Taibbi and Shellenberger calling for someone’s head, try and remember that cybersecurity professionals have a vital and complex role to play in safeguarding the integrity of our digital information ecosystem.
As such, supporting and protecting these professionals while they themselves come under attack is essential as part of the broader effort to maintain the trust which underpins the health of our democratic societies.
Further Reading: Testimony presented by Rand Waltzman before the Senate Armed Services Committee, Subcommittee on Cybersecurity on April 27, 2017.