Reprint: "Security in an Era of Coercive Cyber Attacks"
#IncidentResponse #Consulting
Dear Reader,
The following blog post was originally authored by Jen Weedon and myself and published on FireEye’s blog in May 2015. I am republishing it here in full as I believe the content is still highly relevant to organizations today.

In late 2014, a cyber attack at a major player in the entertainment business prompted an industry wake-up call. The combination of events — an allegedly government-led multi-vector attack intended to embarrass and intimidate a private company through the destruction of company assets, public threats, and the staggered release of stolen information — displayed an unprecedented application of offensive tactics in the cyber arena. The threat actors’ motivations were clear, both in word and in deed: to aggressively and publicly coerce a private company into changing a strategic business decision.
These events galvanized debate over topics that security practitioners and policymakers have long grappled with, including:
How to respond in event of a destructive attack, and the impact of attribution to the response effort
Worry over the proliferation of cyber weapons and actors’ seemingly increased willingness to use them
The roles of the public and private sector in defending against government-sponsored threats
Although this type of scenario was once purely hypothetical and typically only played out by Red Teams during war game exercises, this incident and its implications are arguably watershed occurrences in the history of information warfare in the United States.
This blog post will outline some of the dynamics around destructive attacks and offer concrete steps and best practices that companies can adopt to prepare themselves for an environment where cyber operations are now a tool in everyone’s toolkit.
Why Use Destructive Malware? The Benefits of an Asymmetric Advantage
Destructive cyber activity can be a valuable and low-cost tool for poorly resourced or marginalized actors. This is why destructive cyber weapons are sometimes referred to as “asymmetric” – this type of “weaponry” can cause a significant amount of economic damage without necessarily requiring attackers to expend corresponding amounts of resources. In addition, cyber tools and capabilities may be easier to develop and acquire than other types of weapons, particularly for threat actors contending with prohibitive cost barriers, sanctions, or other factors. The multipurpose nature of cyber capabilities makes them a worthwhile investment by providing a higher rate of return as compared to more conventional warfare.
Cyber tools could also be an attractive option because threat actors may expect a limited response from their victims. Precise, speedy, and conclusive attribution is notoriously difficult and complicated, and may not result in any significant penalty for the threat actors involved. The international community’s challenges with establishing norms of behavior in cyberspace or agreeing on what constitutes a proportional response to a cyber attack, further complicates the efforts of governments to deter or punish actors from engaging in destructive attacks. Without shared standards, threat actors may develop capabilities and conduct cyber operations cheaply, easily, and with minimal risk to themselves, setting implicit standards regarding punishment and deterrence in the process.
Past Examples of Destructive Attacks against Private Companies
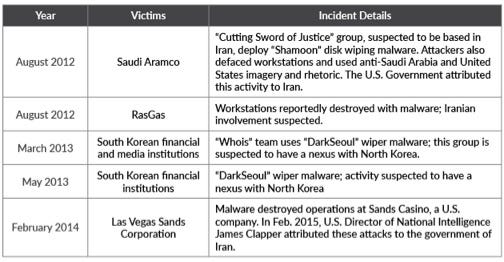
The wanton destruction of victims’ assets is not unheard of in the information security industry, as several high profile cases have been publicized in which the attackers used wiper malware. The destruction of corporate data, especially when accompanied by threatening language, can be particularly alarming to an organization and its employees. The following chart shows some of the publicly reported incidents of destructive attacks:
Despite a common perception of high attacker proficiency, threat actors do not necessarily require a high level of sophistication and technical skill in order to commit a highly destructive attack. However, it should be stated that threat actors may be highly sophisticated with complex intent and motivation – yet may still employ non-sophisticated means to compromise their targets’ networks. Motivation, rather than ability, is often the key differentiator between threat actors that conduct surreptitious data theft and those that seek to commit destructive attacks.
How to Prepare for this New Era of Attacks
Organizations should make the transition from a purely prevention-focused approach to a more comprehensive prevention, detection, and response-focused methodology. Various techniques may be employed to raise the cost of malicious actions to a potential attacker. A comprehensive methodology anticipates, hunts, detects, and responds to threat actors in a dynamic manner, using the appropriate sets of resources, programs, and expertise to match the profile of the business.
To start this conversation off on the right foot, we have compiled some of our best practices and tailored them to directly address destructive situations.
Understanding Actor Motivation and Assessing Organizational Risk
The threat actors we track typically gain enough access to their victims’ networks to conduct a highly destructive attack on corporate assets, should they choose to do so. However, instead of being destructive, most of the threat actors we investigate are focused on cyber espionage: their goal is not to destroy their victims or damage assets, but to breach networks and steal information while remaining undetected. Decisions made by threat actors once the perimeter has been breached depend entirely upon their motivations.
Because an actor’s intent is most often the determining behavioral factor once access has been gained to the target environment, organizations should evaluate their risk profile in light of the threat actor’s possible motivation(s): Who is likely to breach the organization’s defenses, and what do they want to achieve by conducting a breach? When asking these questions, organizations should consider a wide range of potential threat actors, including cyber espionage operators, cyber criminals, hacktivists, and destructive or opportunistic attackers. There are a few different ways that organizations can approach this risk analysis:
A threat-centric approach begins with examining the risks to the organization through the eyes of a potential set of threat actors: How would they view the firm’s operations, and, based on their goals, how might they behave in the environment? Threat intelligence can help organizations prepare for what is most relevant to them, and arm teams who hunt for malicious activity with Indicators of Compromise and anomalous behavior they should be detecting. Red Teaming exercises can help organizations better understand potential threat scenarios and plan appropriate responses.
An asset-centric impact analysis can help organizations identify which business functions are most critical, in order to most effectively plan for and allocate limited resources. For example, if a retailer determines that a short-term interruption in the uptime of its online sales portal would cause an unacceptable loss of revenue, it may elect to invest in DDoS response services to help ensure service availability.
Cyber Attacks: Preparation, Response, and Remediation
Preparation for a cyber attack has mainly been considered within the context of single events. For example, a DDoS attack, a DNS hijacking, or a data breach constitute individual events. A multi-vector attack may be thought of as an ambush across several fronts: it strains defenders’ available resources and can make organizing an effective response quite challenging.
In spite of this complexity, there are concrete steps that may be taken by organizations to protect themselves.
Continuity of Operations
As a start, organizations should identify their core information assets and evaluate the systems necessary to sustain company operations and provide critical services to customers. Duplicating critical data and services to a continuity of operations (COOP) site, cloud provider, or other hosting facility allows flexibility, should it become necessary to establish duplicate replacement infrastructure and quickly bring systems online in the event of an attack. Redundant copies of encrypted data should exist on disparate technologies, in geographically diverse locations, require multifactor authentication, and be configured so that no single set of credentials has access to the “keys to the kingdom.”
During a destructive attack, access to the tools and data needed to conduct an investigation may be hindered. These limitations may include loss of access to or usability of administrator workstations, basic communication channels, and connectivity to the Internet. Establishing redundancy for basic communications like telephone and Internet connectivity is critical. An old-fashioned printed phone tree can be useful in an emergency to help ensure that all teams involved in recovery operations can coordinate their actions.
Defensive Posture
Adjustments may be made to a network’s defensive posture to slow and frustrate an attacker. A flat network is indefensible once a threat actor breaches the perimeter; thus, implementing network segmentation creates firm security boundaries that will contain the spread of wiping or encrypting malware. At the very least, network segmentation will increase the time and effort required by an attacker to reach a large number of systems, multiple sites, and critical systems.
Multiple domains or forests with properly configured trust relationships allowing the least amount of access possible, (known as a “deny all” policy), is advised. In addition, situating security products at critical internal junctures to add finely-grained control and monitoring capabilities to servers and other enclaves containing high-value assets (e.g., Human Resources or Accounting) can provide an essential added layer of protection.
Response
When called to duty, incident responders work through a period of assessing the situation. Our consultants work with the client’s unique business footprint and risk tolerances to develop a comprehensive plan to investigate, respond, and remediate various types of attacks, including those of a catastrophic nature. At times, immediate remediation activity must take place given the nature of a certain forms data exposure, and certain steps involved in the remedial process may be delayed while investigators collect additional evidence. Ultimately, the decision to remediate or discuss whether or not to pursue a certain course of action, if the actor has done or may do something destructive, is something clients should discuss with their incident response team.
Law Enforcement Involvement
A strong Incident Response Plan should fully outline the steps needed to respond to a compromise, and should include an understanding of what will be needed once law enforcement becomes involved in the situation. Such a plan may leverage a playbook or an Escalation Matrix to define who will coordinate with law enforcement, and at what point.
Once a decision is made to involve law enforcement, organizations should take the following steps:
Preserve evidence of the attack, to include logs, hard drives, email, and any other information that might capture the details of the attack.
Any compromised systems should be secured to avoid the alteration or destruction of data.
Maintain a chain of custody to show that evidence has been properly handled before it is handed over for investigation.
All personnel involved with responding to an incident should document what occurred, when it was discovered, how it was discovered, and other relevant details.
Managing Crisis in the Public Eye
It is important for organizations to develop a Public Relations (PR) strategy that provides guidance regarding how to respond in the event that a breach goes public and that threat actors are simultaneously engaging publicly with the media.
It is difficult to anticipate exactly how a public disclosure incident will play out; however, internally defined PR guidelines can set the principles that will guide a firm’s response when it is in the spotlight. A PR strategy should define which questions the organization will or will not answer, the handling of press inquiries, response timing, response channels (e.g., official press release, social media participation) and the internal and external stakeholders that should be engaged. In the event of such a crisis, it will reduce the difficulties that organizations will face to control the message, respond appropriately, and refine their public response as the crisis unfolds.
One of the most important components of a PR strategy comes early in the response timeline: how the business chooses to initially acknowledge the incident and frame it in the public eye. This initial acknowledgement must be chosen carefully, as it often sets the tone and often dictates how the public perceives the organization at every stage of media coverage. Organizations should consider the possibility that actors may seek to further sensationalize the incident with embarrassing disclosures, or leaks that might taint the firm’s public message. In order to get ahead of this, some businesses may choose to more thoroughly explain the potential impacts of a breach—either publicly, or on a selective basis to important clients and partners—thereby squashing potential criticisms or fallout before they become an issue. While this approach may or may not be appropriate for any given organization, PR strategies should account for the possibility that the business will have to wrestle for control of the message as threat actors attempt to manipulate public perception.
By considering their public response to a broad range of possible breach scenarios, organizations can strengthen their ability to respond to crisis. A thorough PR strategy, composed before a crisis hits, will ensure that the firm’s public response protects its equities and sends the right message to the firm’s most important clients and stakeholders.
Cyber Insurance
Cyber risk management has emerged as a priority for the executive suites of many companies in the private sector in the wake of 2014’s high profile breaches. As organizations seek to supplement their risk mitigation programs, cyber insurance has become an increasingly popular way for businesses to limit the potential losses incurred by a major incident.
Rapid growth in the cyber insurance market may spur a quiet but forceful shift in the near future. The insurance industry will likely become influential in determining security best practices, and will drive companies to adopt those practices. As organizations turn to insurers to absorb losses from their breaches, insurers will likely begin defining more rigorous minimum security standards for their policyholders. In turn, organizations that want to ensure that they are covered will be required to comply with these standards or a general standard of care. Without measurable adherence to these theoretical standards, organizations risk paying higher premiums or losing coverage all together.
While the increasing importance of insurance in the security ecosystem has long been predicted, recent events have set the scene for cyber insurance to transform from a niche offering into a perceived necessity, and for insurers to emerge as powerful influencers in the security industry as a result.
Conclusion
In conclusion, the incident discussed in this article sparked self-examination among the security community and corporate and government leadership, and will leave an indelible mark on the security landscape. We have now seen cyber security discussed at the highest levels of government and private sector leadership. This incident highlighted one of the most complex aspects of this field: cyber security is inherently a multidisciplinary challenge. It is not a technical issue for the IT department alone; it is a topic that can have profound implications for business operations, reputation, law, international relations, public relations, public policy, and other disciplines. Organizations would do well to develop comprehensive planning to ensure the survivability of the business in the event of a cyber attack.
[i] Suciu, Peter. “Why Cyber Warfare is so Attractive to Small Nations.” Fortune. 21 Dec. 2014. Web. 14 Jan. 2014.
[ii] "Guide for Conducting Risk Assessments." National Institute of Standards and Technology, U.S. Government. Sept. 2012. Web. 12 Jan. 2015.
[iii] “Electronic Crime Scene Investigation: A Guide for First Responders, Second Edition.” Department of Justice, U.S. Government. April 2008. Web. 26 Feb. 2015.
[iv] "Is Your Company Ready for a Big Data Breach?" Ponemon Institute. Sept. 2014. Web. 26 Feb. 2015.
[v] Bennett, Cory. "Demand for Cyber Insurance Skyrockets." The Hill. Jan. 15, 2015. Web. 26 Feb. 2015.