The Spy Who Tried to Silence Me
"Kyiv's Most Dangerous Man" claimed to expose Russian influence operations while apparently running one himself.
I finished most of this investigation in June 2025. I chose not to publish it.
As a researcher who tracks foreign influence operations, I’ve learned that exposure can change behavior. I wanted to observe what would happen when a suspected operation knew or strongly suspected they were about to be identified. Would they adjust tactics? Disappear? Double down?
The response itself would be evidence.

The Experiment
When I began asking questions about credentials and connections, the reaction was immediate and hostile. Within 24 hours, professional discourse degraded into personal attacks and psychiatric diagnoses.
Network accounts quickly appeared to coordinate defense. The apparent playbook was to discredit the researcher, not the research.
One month later, a strategic exit disguised as escalation: a final article published on July 9, 2025, calling for the most aggressive possible action against Russian assets. Maximum pro-Ukrainian positioning. Buried within it was language describing the author as a victim of “targeted harassment, smear campaigns, and coordinated efforts to discredit, demoralize, and silence us.”
This appeared to me as some type of pre-emptive shield; inoculation against the exposure to come.
Then, silence.
Before: Prolific output, sophisticated content, multiple posts per week.
After: Four months of absolute silence on their primary platform.
Legitimate voices don’t retreat when questioned. Operations do.
Why Now?
I’ve given this five months to demonstrate my concerns were unfounded. Instead, the silence continues. The patterns I documented have only been reinforced by what followed–or rather, by what didn’t.
What you’re about to read was written in June 2025. Its publication today completes a story the original analysis couldn’t: what happens when a spy realizes they’ve been made.
Sometimes the most damning evidence is what comes after exposure.
Let’s examine what came before it.
Author’s Note: Measurement of the impact of this influence operation is outside the scope of this analysis.
The Curious Case of Grant Wescott
This report documents my encounter with an individual presenting himself as “Grant Wescott,” an American defense consultant allegedly based in Ukraine, who appears to be conducting a covert operation.
Through detailed examination of his social media activity, published content, and network associations, I present evidence suggesting this persona represents a new evolution in information warfare: one that targets not just what we think, but how we analyze threats. The case shows several concerning patterns: unverifiable credentials, coordinated network amplification, systematic deflection from Russian activities, and the deployment of psychological warfare techniques consistent with Russian doctrine while maintaining pro-Ukrainian facade.
As someone who publicly tracks foreign influence operations and online extremism through my cybersecurity and threat research work, I have unfortunately become a frequent target of the very actors I investigate. These individuals typically respond defensively to my research and use my social media posts as opportunities to manipulate my audience by injecting counter-narratives to those threads. The individual presenting himself as “Grant Wescott” appeared not to anticipate that I would detect his interference tactics.
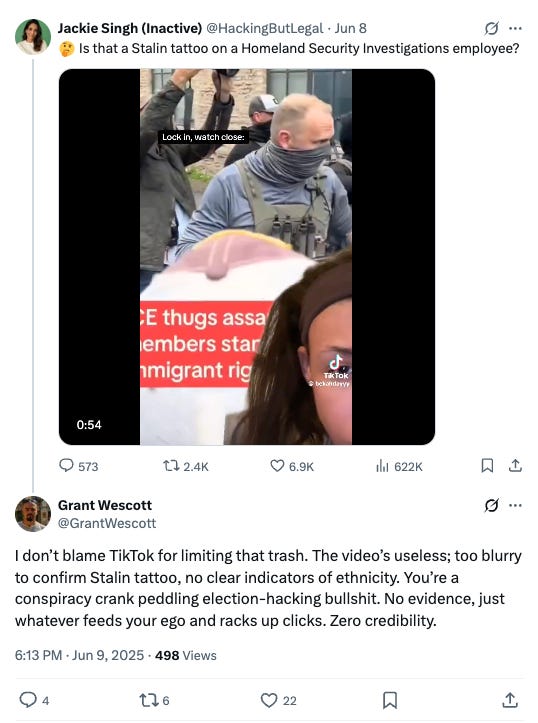
This case began when I posted a TikTok video showing a recent Immigration and Customs Enforcement arrest which appeared to show an agent sporting a prominent tattoo of Joseph Stalin on his forearm, a concerning indicator of potential foreign extremist infiltration in law enforcement during a time of heightened political repression and a visible rise in the use of aggressive tactics by U.S. immigration enforcement.
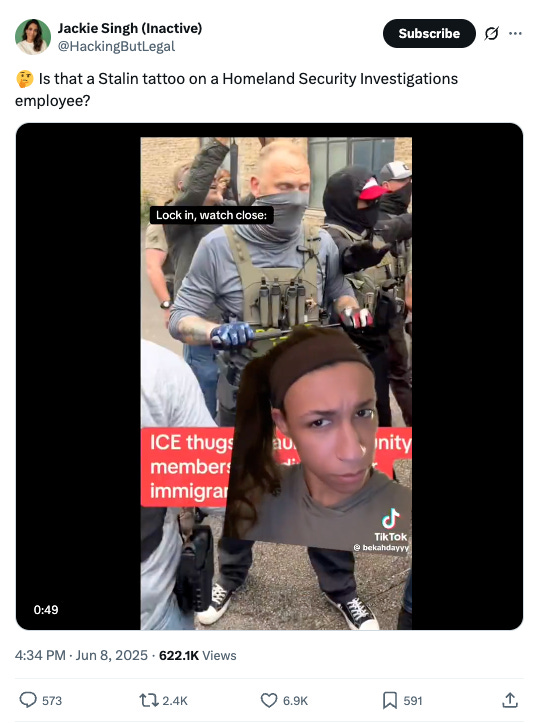
Given my work, I’ve grown accustomed to defensive responses from threat actors, but what followed revealed something more calculated.
A Constructed Persona
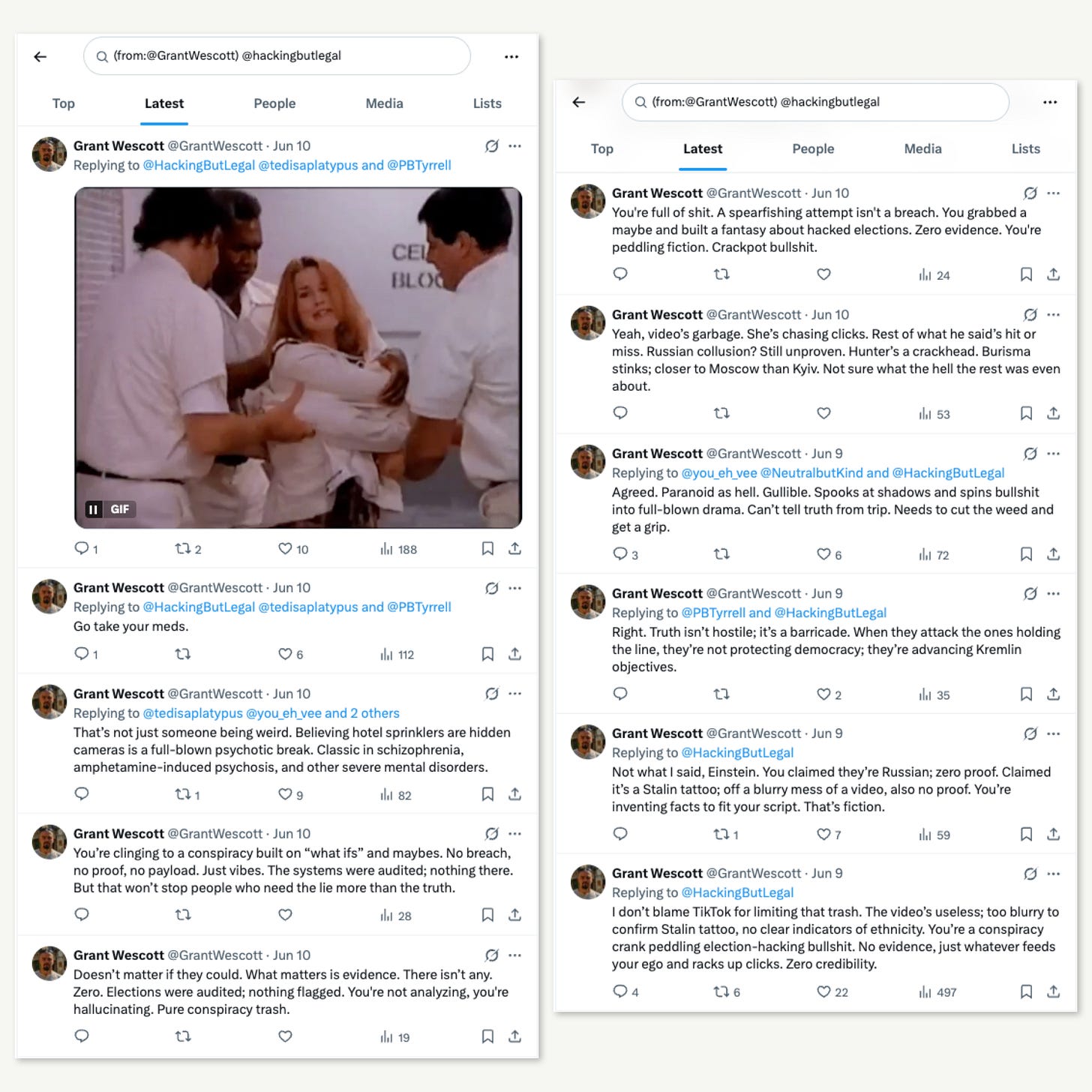
Grant Wescott’s reply came approximately 15 hours after my initial post:
I don’t blame TikTok for limiting that trash. The video’s useless; too blurry to confirm Stalin tattoo, no clear indicators of ethnicity. You’re a conspiracy crank peddling election-hacking bullshit. No evidence, just whatever feeds your ego and racks up clicks. Zero credibility.
This calculated response followed a pattern I’ve come to recognize from intelligence operatives who could be triggered by the virality of a post or might be monitoring the accounts of those who post about political topics.
Wescott’s intial deflection from substantive security concerns through irrelevant technical objections while launching a personal attack exemplifies the Russian style to which I have become accustomed: operations designed to influence perceptions and decision-making rather than simply gather intelligence. Wescott seemed to overplay his hand, not realizing his defensive response would reveal the very manipulation tactics he was attempting to deploy.
Investigating his background revealed several red flags.
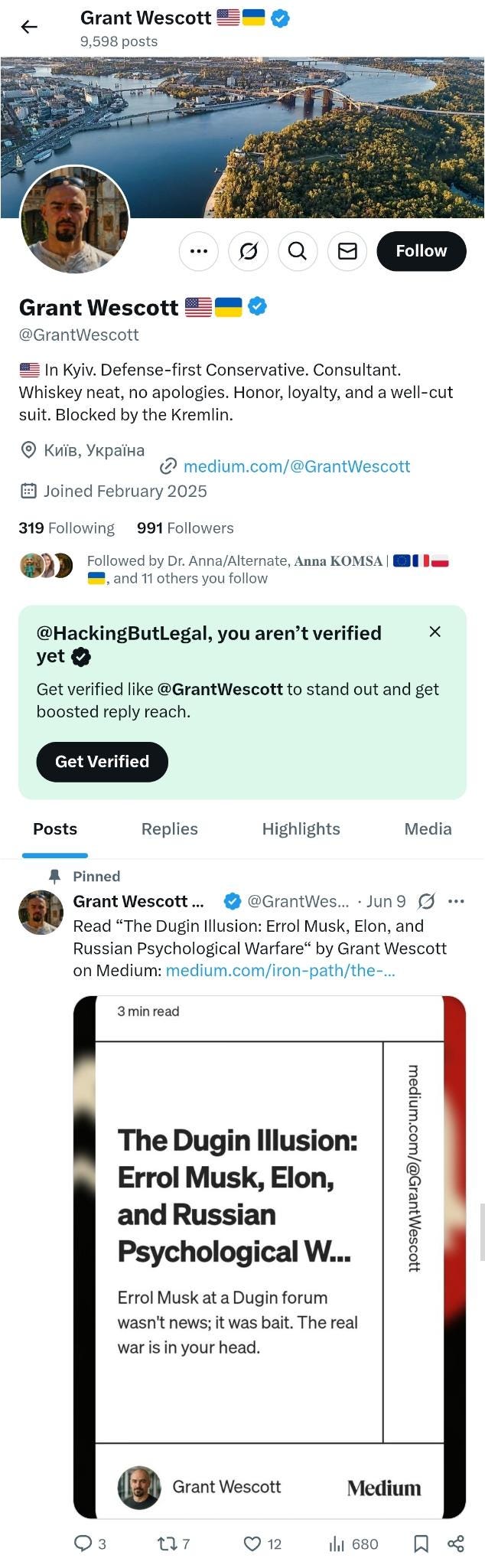
His X profile (@GrantWescott) presents him as an “American defense consultant in Kyiv” and “tactical strategist” with the aggressive tagline “loyal, lethal, and never off the clock.” The profile displays American and Ukrainian flag emojis, a verification checkmark, and shows 9,598 posts.
Most tellingly, his article “The Dugin Illusion: Errol Musk, Elon, and Russian Psychological Warfare” was pinned to the top of his feed. Pinning is an intentional act, suggesting the piece was central to his messaging strategy at the time.
Author’s Note: As of the publishing of this report, the X account’s biographical details have been updated to read, “Kyiv’s Most Dangerous Man. Texan. Reaganite. Whiskey neat, no apologies. Honor, loyalty, and a well-cut suit.”
The flag emojis have been removed, and the verification checkmark is no more. More than 7,000 new tweets have been posted by the account.
Despite extensive claims of expertise, attempts to verify Wescott’s professional credentials proved fruitless. A LinkedIn search returned only a handful of individuals named Grant Wescott, none matching his stated background. The absence is striking given that most public professionals claiming defense expertise maintain discoverable online presence. Moreover, his tagline “No noise, just results” directly contradicts his aggressive response to my post. It is my experience that most legitimate consultants typically avoid inflammatory public confrontations.
His publication “Iron Path,” hosted on Medium, claims to provide “brutal clarity from Ukraine’s front” while promising to expose “psyops” and highlight “the West’s failures.” The framing suggests systematic undermining rather than the constructive criticism which is more typical of legitimate Ukrainian sources.
Medium is a strategic platform choice for this operation. The publishing platform provides automatic credibility through association with independent journalism, algorithmic amplification through its recommendation system, plausible deniability as grassroots activity, professional formatting without technical infrastructure, and audience segmentation through tagging. By operating within an established platform rather than creating independent infrastructure, an operation can easily avoid digital forensics that might reveal coordination or funding sources.
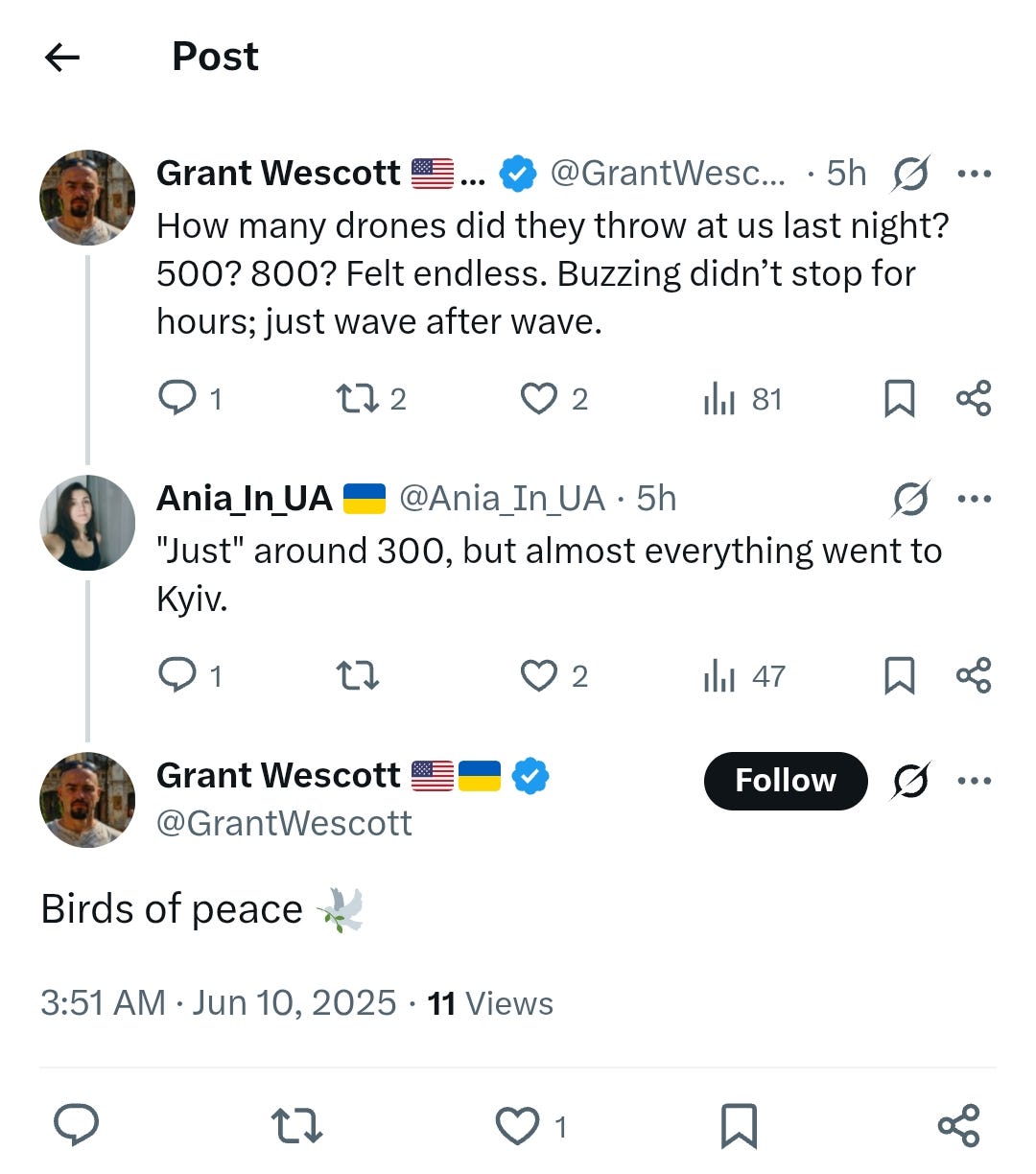
Wescott’s facade becomes even more apparent when examining his social media behavior. A particularly revealing post appeared following a recent drone attack on Kyiv:
How many drones did they throw at us last night? 500? 800? Felt endless. Buzzing didn’t stop for hours; just wave after wave.
That post was followed by a reply to a Ukrainian user:
Birds of peace 🕊️
Because the war drones in this context were sent by Russia to Ukraine, the content reads like “experiential” battlefield reporting which is slyly intended to valorize Russia’s attacks, followed by a reply which suggestively mocks Ukrainian suffering.
Such content is only part of a wider and more concerning pattern of Wescott presenting himself as a pro-Ukrainian voice while his actual posts suggest callous disregard for Ukrainian casualties. This contradiction–namely, maintaining a supportive facade while subtly undermining the legitimate cause–would be characteristic of an intelligence operation designed to infiltrate and manipulate pro-Ukrainian discourse.
A Campaign of Meta-Manipulation
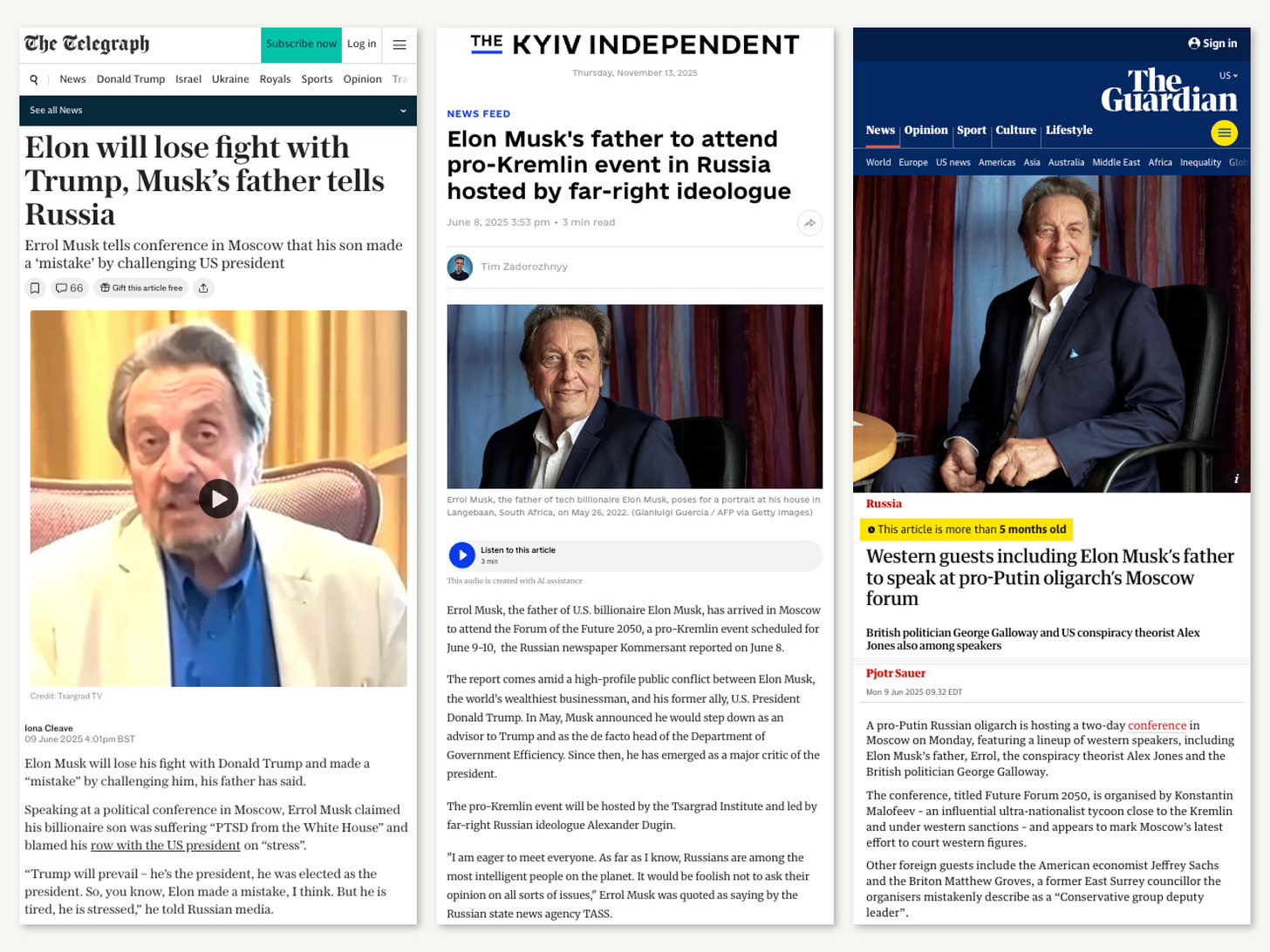
On June 9, 2025, Wescott published his pinned article, which appears to be an example of “meta-manipulation”: appearing to expose influence techniques while employing them. The piece claims that Errol Musk’s appearance at Alexander Dugin’s forum was merely psychological “bait” creating an “illusion,” a position that directly contradicts both factual reporting and common sense.
The timing reveals potential coordination. Major news outlets including The Telegraph, The Guardian, and The Kyiv Independent had confirmed that same day that Errol Musk actually attended the pro-Kremlin “Future Forum 2050,” sat alongside Russian Foreign Minister Sergei Lavrov, and praised Putin as “very stable and pleasant.”¹²³
Wescott’s article appeared to be a ‘rapid response’ designed to reframe legitimate news coverage as psychological manipulation.
By framing documented Russian influence events as “illusion,” Wescott deflects attention from real counterintelligence concerns while also appearing to provide legitimate analysis. The technique is to manipulate an opponent’s decision making by controlling their perception of the situation.
I noted that Wescott’s Dugin article employs several concerning tactics:
It creates assumed complicity with statements like “You believed it for a moment. Everyone did,” positioning readers as already compromised. It deliberately undermines cognitive confidence with phrases like “Your own mind becomes the broadcast tower,” eroding trust in analytical capabilities while positioning Wescott as uniquely qualified to interpret reality.
Most troubling of all is his warning “Don’t be their agent. Don’t think their thoughts” which is programming disguised as protection.
Patterns of Coordination and Escalation
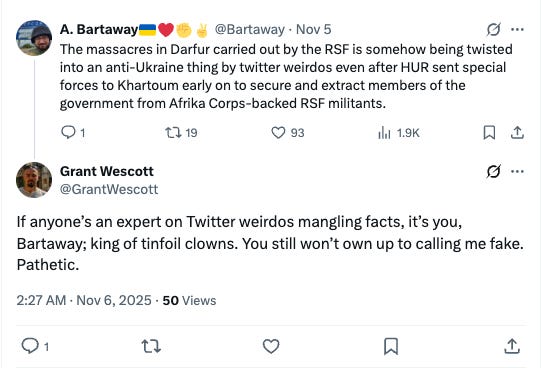
My continued exchanges with Wescott revealed standard patterns from coordinated intelligence operations targeting my social media posts. When I suggested I could prove my concerns about his activities, his responses escalated from intellectual discourse to personal attacks: “Go take your meds.”
This degradation when pressured is characteristic of operatives whose cover is being systematically exposed; and it wasn’t his first time clapping back at an accusation of inauthenticity, as you can see below.
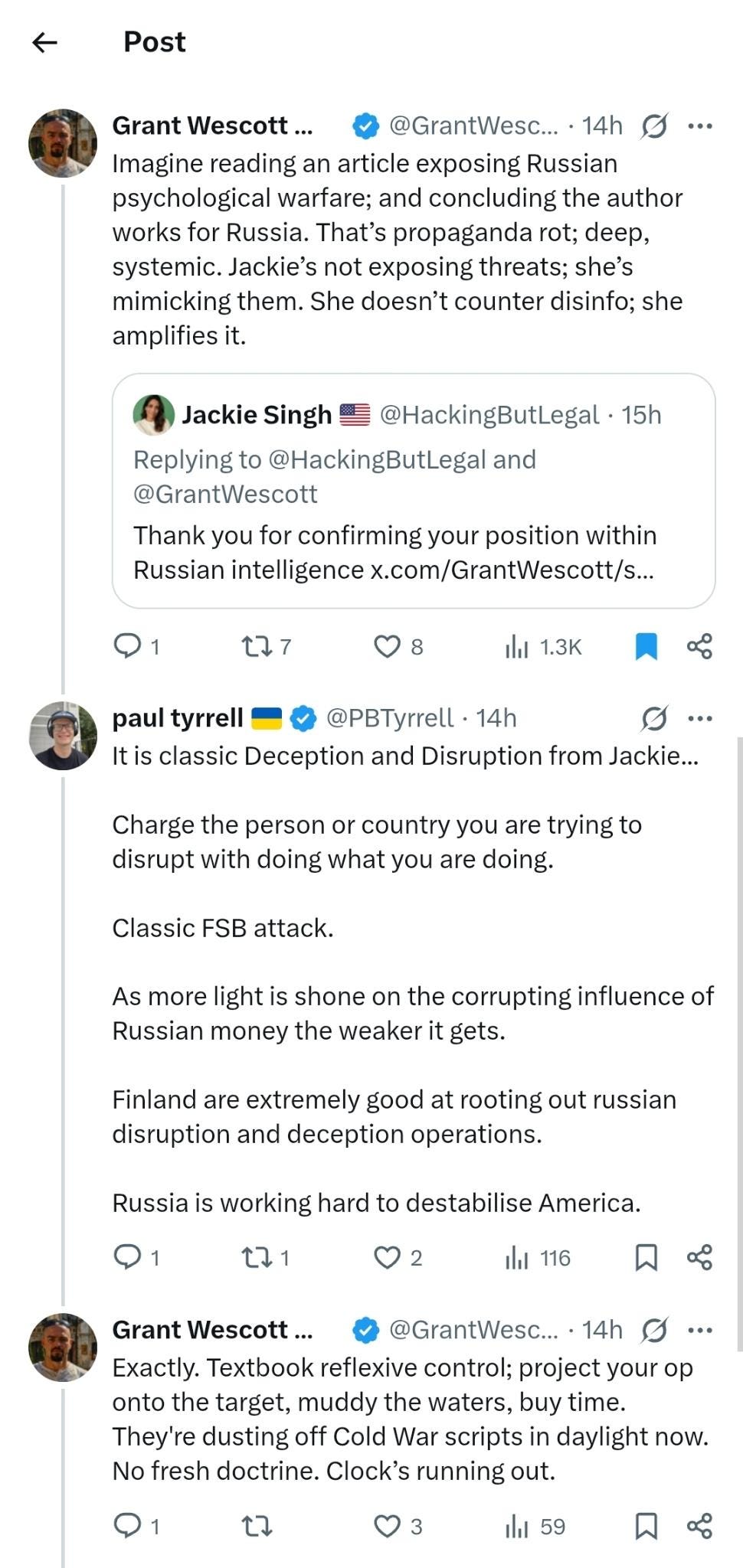
When confronted about a potential covert Russian connection, Wescott employed inversion tactics: “Imagine reading an article exposing Russian psychological warfare; and concluding the author works for Russia. That’s propaganda rot; deep, systemic. Jackie’s not exposing threats; she’s mimicking them. She doesn’t counter disinfo; she amplifies it.”
His specific targeting of my work as “mimicking” threats rather than exposing them is a common deflection tactic used by operatives to discredit researchers who get too close to actual operations.
Evidence of network coordination emerged when another account, Paul Tyrrell (@PBTyrrell), became vehemently defensive during our exchanges, making statements like “It is classic Deception and Disruption from Jackie” and “Classic FSB attack.”
Tyrrell escalated his accusations: “Charge the person or country you are trying to disrupt with doing what you are doing. Classic FSB attack. As more light is shone on the corrupting influence of Russian money the weaker it gets.”
What made this coordination particularly suspicious was the speed at which Tyrrell appeared to defend Wescott and attack my research. He then followed me to other threads, reinforcing their pair narrative that I, the researcher, was the actual threat actor engaged in deception and disruption operations.
In my assessment, these behavioral patterns are consistent with sockpuppet networks involving multiple accounts working together to amplify messaging and defend primary personas when challenged, and the network behavior is consistent with a wider operation designed to protect a primary asset through secondary account amplification.
PsyOps and Strategic Cover
Subsequent analysis of Wescott’s complete published corpus on his Medium-hosted “Iron Path” publication reveals a psychological warfare operation that extends beyond simple disinformation. His content demonstrates systematic deployment of techniques designed to fragment Western unity and demoralize audiences supporting Ukrainian resistance.
On the surface, the content appears decisively pro-Ukraine.
However, further analysis reveals an undercurrent which wholly contradicts this initial evaluation.
Arsenal of Manipulation
Wescott’s writing employs emotional weaponization: psychological manipulation which far transcends advocacy. In his piece “Rhetorical Indictment,” (self-published, but not to the “Iron Path” publication) he states: “There is no neutral. There is no middle ground. There is no nuance.”
This type of approach is designed to trigger fight-or-flight responses which present opportunities to slip poisoned narratives right past our ability to perform rational analysis.
Wescot’s piece “Gas, Silence, and Graves” exemplifies the technique: “Europe fuels the killing. Every euro burns just as surely as the shells it buys.” Certain text is strategically bolded throughout the piece.
Extreme emotional language is designed to overwhelm cognitive defenses and manipulate our decision-making through pure emotional saturation (See: Bannon’s “flooding the zone”). Absolute binary framing tends to eliminates nuanced thinking. This “moral guillotine” type of technique mirrors totalitarian rhetoric designed to collapse democratic discourse into simplified us-versus-them frameworks. By eliminating the possibility of reasonable disagreement, it destabilizes the cognitive foundations necessary for democratic deliberation.
Most concerning is Wescott’s systematic deployment of nihilistic messaging designed to demoralize Western audiences. In “Strategic Inaction, Tactical Betrayal,” he declares: “There is no peace deal coming. No honest broker in the Kremlin. No ‘off ramp’ that leads to anything but further butchery.”
While likely factually accurate about Russian intentions, such messaging serves Russian objectives by promoting learned helplessness and strategic paralysis among Western populations.
This psychological state benefits Russian aggression.
Strategic Tribal Exploitation: Elon Musk
Wescott’s Elon Musk coverage demonstrates sophisticated audience manipulation through managed narrative progression. In his positive piece “Elon Musk: The Man Who didn’t Fold,” he positions Musk as a victim of ‘coordinated resistance,’ creating protective narratives around a potentially compromised figure. Through the use of statements like, “Where others postured, Musk advanced” and “He doesn’t ask permission. He sets the tempo,” the piece targets conservative psychological vulnerabilities, particularly those feeling marginalized by institutions or a changing culture, more broadly. By presenting Musk as a victim of “coordinated resistance” from “legacy actors,” Wescott exploits existing grievances to build protective narratives around figures who may themselves be subject to influence operations.
While it may be itself unusual to frame Elon Musk in a positive light despite, among other issues, his reported direct dealings with Vladimir Putin and harmful interference of Starlink’s operation in Ukraine, this apparent defense serves multiple strategic purposes beyond simple pro-Musk messaging.
By positioning Musk as someone who “broke the cartel” and “confronted suppression directly,” Wescott creates a narrative framework that discourages critical examination of Musk’s actual activities. The piece functions as inoculation against legitimate concerns about foreign influence by reframing such concerns as persecution of independent voices.
His subsequent critical piece “I Can’t Unsee What Elon Musk Just Said,” in which he claims to be disturbed by Musk’s alleged comments about Trump and Jeffrey Epstein, employs a more sophisticated tactic. By positioning himself as a conservative genuinely troubled by Musk’s statements, Wescott creates apparent credibility through internal conflict while actually managing how his audience processes damaging information. This sequence achieves multiple objectives: establishes trustworthiness through willingness to criticize allies, controls revelation of damaging information, tests tribal loyalty, and inoculates audiences against future revelations.
The piece begins: “I’m a conservative. I believe in draining the swamp, taking down the elites, protecting the innocent, and fixing this broken system. But then Elon Musk dropped a post that hit me like a truck.” The opening creates identification with conservative audiences before introducing cognitive dissonance.
By positioning himself as someone genuinely struggling with uncomfortable information about figures he previously supported, Wescott attempts to create several strategic advantages:
Credibility through apparent internal conflict: Shows willingness to criticize allies, establishing trustworthiness
Controlled revelation: Manages how damaging information is processed by target audiences
Testing of tribal loyalty: Creates framework for audiences to process threatening information without abandoning core loyalties
Narrative inoculation: Prepares audiences to dismiss future revelations as already considered and processed
The timing of the story, published shortly after increased scrutiny of Musk family connections to Russian influence networks, suggests strategic protective messaging rather than organic advocacy.
Together, Wescott’s pieces about Elon Musk function as protective messaging management around a figure under influence operation scrutiny.
False Equivalence (About Stalin)
Wescott’s treatment of Josef Stalin reveals particularly sophisticated manipulation. His personal ideology and feelings about Stalin may have been the trigger which led him to respond to my tweet about the officer with a suspected Stalin tattoo.
While Wescott’s piece “In 1941, Stalin Sent a Telegram,” presents strong anti-Stalin rhetoric, his overall approach serves as “inoculation propaganda” through the use of legitimate criticism of past Russian authoritarianism to deflect attention from contemporary Russian activities while undermining Western resolve.
While appearing to criticize Soviet dictator Josef Stalin, he creates false equivalencies stating “Stalin and Hitler weren’t opposites. They were mirrors.”
This narrative reduces complex historical understanding in ways that serve contemporary Russian strategic objectives. By diminishing recognition of Soviet sacrifice while promoting fatalistic acceptance of Russian imperial behavior, he creates a cognitive framework that benefits current Russian operations. His anti-Stalin stance functions as credibility establishment while his broader messaging promotes fatalistic narratives about unchanging Russian behavior.
By positioning Russia as perpetually dependent yet dangerous, he creates resentment narratives that paradoxically serve Russian victimhood strategies while discouraging robust Western responses.
Target Fragmentation
Wescott’s content appears designed to fracture Western unity through multiple simultaneous vectors. His systematic attacks on European resolve position America as superior but betrayed, driving wedges into transatlantic relationships. The messaging exploits both progressive guilt and conservative nationalism, demonstrating advanced understanding of how to fragment audiences along existing ideological fault lines.
The content targets faith in democratic institutions and diplomatic processes, promoting institutional delegitimization while overwhelming audiences with crisis language designed to promote cognitive exhaustion and disengagement. The tribal manipulation evident throughout his corpus uses the same events and threats but presents them with entirely different emotional frameworks depending on which audience segment is being targeted. Progressives receive guilt-inducing narratives about complicity, while conservatives receive betrayal narratives about weakness.
The desired effect: erosion of unified Western response to Russian aggression.
Targeting Our Analytical Frameworks
What makes this case concerning is how it represents a small sample of the type of disinformation which targets analytical frameworks in use by both security professionals and highly informed citizens. While many traditional disinformation operations promote specific false narratives, this operation is also partly designed to undermine our ability to conduct threat analysis altogether.
By positioning himself as an expert on Russian psychological warfare while potentially executing it, Wescott seeks to create several strategic advantages:
Induce analytical paralysis where researchers become hesitant to trust their pattern recognition.
Create authority dependency by positioning the operation as the sole reliable source for interpreting information.
Create meta-confusion where the boundary between authentic counterintelligence education and influence operations becomes deliberately blurred.
Position himself as a trusted persona on the Ukraine side of Russia’s war of aggression in order to infiltrate and surveil networks and events.
Disrupt legitimate investigations by reframing counterintelligence work as evidence of successful Russian manipulation, which is what Wescott attempted in his replies to me.
Several factors suggest Wescott represents an intelligence operation:
Operational knowledge combined with misdirection: Professional-grade understanding of psychological warfare techniques used to deflect from documented Russian activities
Systematic protection of Russian interests: Consistent deflection from documented influence activities while appearing to provide counter-intelligence analysis
Constructed persona indicators: Unverifiable professional claims combined with behavior inconsistent with legitimate expertise
Network amplification: Coordination with accounts that defend his activities and follow critics to other discussions
Temporal and tactical claims: Unverifiable battlefield reporting that serves to build credibility
Advanced psychological manipulation: Deployment of influence techniques against Western audiences while maintaining pro-Ukrainian facade
Strategic timing coordination: Publication patterns that align with geopolitical events and Russian strategic objectives
Tribal exploitation capabilities: Advanced understanding of different audience psychographics and targeted messaging strategies
Platform exploitation: Strategic use of Medium to gain credibility and reach targeted audiences
Assessment: High Probability Coordinated Operation
The comprehensive analysis reveals patterns consistent with an influence operation with multiple strategic objectives:
Primary Objectives:
Demoralize Western populations regarding Ukraine support sustainability
Fragment Western unity through targeted emotional manipulation
Degrade trust in democratic institutions and analytical capabilities
Promote nihilistic worldview that benefits authoritarian narratives
Protect Russian influence activities from legitimate investigation
Manage information flows around potentially compromised figures through protective messaging
Operational Characteristics:
Multi-platform narrative coordination with Medium-hosted “Iron Path” publication
Psychological profiling and targeted audience manipulation across political spectrums
“Controlled opposition” techniques employing pro-Ukrainian facade
Advanced understanding of Western cognitive vulnerabilities and tribal dynamics
Network amplification through coordinated accounts
Strategic timing aligned with geopolitical events and potential damage control needs
Protective messaging for figures under influence operation scrutiny
Platform exploitation for credibility and audience targeting
The Strategic Exit: When the Operation Went Dark
While Wescott’s Medium publication remained silent through the fall, his final article before that silence is revealing. On July 9, 2025, exactly one month after our initial exchanges, he published “No More Excuses: Seize Every Russian Asset Now”, his most aggressively anti-Russian piece yet, calling for total seizure of Russian assets and maximum pressure on the Kremlin.
The timing and content suggest strategic calculation. The piece positioned him at maximum pro-Ukrainian, anti-Russian advocacy–the strongest possible inoculation against accusations of serving Russian interests.
Most revealing was this passage:
“Russia doesn’t want anyone to know the truth — especially their own. Journalists, social media users, even regular people like me have faced serious backlash: targeted harassment, smear campaigns, and coordinated efforts to discredit, demoralize, and silence us.”
He was describing exactly what he did to me just weeks earlier, all the while preemptively framing himself as a victim of those same tactics. Classic inoculation: position yourself as the target of the very operations you’re running, so when exposure comes, you can claim persecution.
Then came the silence.
Before July 9, 2025:
30+ articles published March-July
Multiple posts per week
Consistent sophisticated content
Professional production quality
After July 9, 2025:
Zero Medium articles for 4+ months
Account remains active but dormant
No explanation for the cessation
Complete departure from previous prolific pattern
The silence was not total; it was selectively applied to his Medium publication. Meanwhile, Wescott continued posting on X (Twitter) at a voluminous rate.
On October 31, 2025, Wescott claimed upcoming attendance at the European Defense Tech Hackathon in Kyiv (November 6-9, 2025), a highly technical event primarily focused on the development of drone interception technologies to fight Russian aggression.

This claim reveals operational adjustment rather than simple abandonment.
Wescott ceased publishing the influence content that could have drawn added scrutiny while maintaining tactical credibility through a technical, military-adjacent activity. Unlike his other unverifiable or difficult-to-verify claims, this one has specific dates, named organizers, and documented participants, meaning it is perhaps theoretically verifiable.
The security implications warrant serious attention.
If Wescott did attend, questions arise about who vetted his credentials for access to sensitive European military drone defense technology. What information was gathered? Who received reports? If the claim is fabricated, why maintain cover through false attendance at military-technical events while avoiding the long-form content that previously defined his persona?
This pattern mirrors operational doctrine: cease suspicious activity, maintain minimal credible presence, preserve the asset for potential future use. The choice of a technical military event rather than resuming Medium publication suggests an operational priority of maintaining access to military/defense circles while staying below the radar of influence operation researchers.
He did not post further information about the event.
Did anyone at the November 6-9, 2025 European Defense Tech Hackathon in Kyiv actually meet “Grant Wescott”?
Unmasking Wolf
This week, I was able to obtain definitive confirmation: “Grant Wescott” is Gregory Richard Wolf (DOB: 06/08/1982), a convicted felon.
Ohio court records from 2003-2015 document a consistent and escalating pattern of serious criminal conduct: breaking and entering with arson charges (2003), domestic violence conviction with probation and substance abuse monitoring (2010), ongoing compliance violations, and disorderly conduct intoxication (2014).
The cumulative effect likely left Wolf unemployable through legitimate channels.
Wolf’s documented Ohio residence, his social media handles, webite, and accounts positioning him in Kyiv and Denver all share consistent identifier patterns. His company Wolf Cybersec, LLC appears in Colorado business records with a lapsed corporate registration as of 2021, as do Gnarly Wolf Productions, LLC, Wolf Dynamics, Ltd, XCELERANT Services LTD, Ravenwire Films Ltd, Grey Wolf Photography, LLC, and Cynical Systems, LLC, all with lapsed business registrations and varying addresses in Colorado, mostly in Denver.
In at least one case, one corporate entity is listed as an owner or agent of another.
Integration Into Broader Disinformation
Wolf appears as a named “perpetrator” on georgianlegion[.]help (domain registration in February 2025), an astroturfing construction with a professional look which is designed to delegitimize Ukrainian volunteer military units and diaspora fundraising networks.
This site is itself sophisticated disinformation infrastructure. It features press and law enforcement liaison channels, fabricated institutional legitimacy, and narrative-driven “victim collection” designed to appear as grassroots investigation while actually functioning as a strategic funnel for the Kremlin.
Wolf’s prominent placement on this platform cannot be coincidental.
By positioning him as an established Georgian Legion critic, the site lends operational credibility to his other activities. This simultaneously amplifies his criticism into delegitimizing valuable narratives about Ukrainian resistance networks. This means either coordination with a broader infrastructure attacking pro-Ukraine causes, or tactical participation in operations that serve Russian strategic objectives, regardless of Wolf’s stated positioning.
Both scenarios indicate Wolf’s operational utility extends beyond social media discourse into systematic delegitimization of Ukrainian institutional structures with an underlying intention of undermining Western support for Ukrainian military effectiveness at a structural level.
Why Wolf Was Recruitment-Viable
Gregory Wolf’s criminal history reveals the exact vulnerability profile intelligence services exploit: chronic financial desperation, documented substance abuse, trouble with the law, and unemployment barriers created by felony convictions. Someone with this background who is suddenly relocated internationally alongside hints of operational infrastructure and income does not represent rehabilitation, but recruitment.
Wolf’s possible technical competence combined with complete absence of legitimate employment prospects made him operationally valuable. His psychological profile: resistance to authority, basic capability to compartmentalize, and his impulse control issues could have suggested his susceptibility to directional oversight to anyone watching.
The FSB Assessment
A source who works closely with Ukrainian Security Services has informed me that their assessment is unequivocal: Wolf receives funding from Russia’s Federal Security Service.
According to these officials, Wolf operates as a directed asset.
“He’s definitely paid by the FSB. They have a type”
“It’s always the so-called cybersecurity guys”
This assessment is based on intelligence collection conducted by security services with operational presence in Kyiv while Wolf was physically located in Kyiv.
While Ukrainian officials have not publicly confirmed this evaluation, and Russian security services will deny any connection, the alignment between this assessment and the behavioral patterns documented throughout this investigation provides substantial corroboration.
Operational Reality
The gap between “Gregory Wolf, Ohio felon” and “Grant Wescott, sophisticated defense consultant and tactical strategist” is quite wide. What we’re seeing is operational cover, the construction of a persona designed to infiltrate, deceive, and undermine.
Wolf’s vulnerabilities provided the recruitment vector. His technical skills provided operational value. His desperation provided motivation. His psychological profile provided susceptibility to direction. His silence since July 2025 suggests either operational pause pending reassessment or repositioning for renewed activities.
The operative question is no longer “Is this an intelligence operation?” but rather, “Who else operates within this infrastructure, and what information has been compromised?”
Case Study in Evolving Threats
This case illustrates how operations target our analytical frameworks themselves, not just our beliefs. Increasingly, campaigns protect suspicious activities by compromising our ability to conduct threat analysis.
Key indicators evident in this case:
Claims of expertise without verifiable credentials
Teaching about threats while discouraging specific investigations
Escalation to personal attacks when challenged with substantive questions
Protective messaging for potentially compromised figures
Managed information flows designed to maintain audience loyalty while controlling damage
Most importantly, we must develop comfort with uncertainty while maintaining analytical rigor. Campaigns in non-linear warfare often seek to create confusion and paralysis rather than promote specific beliefs. Recognizing this pattern allows us to continue legitimate threat analysis while remaining appropriately skeptical of those who claim unique authority to interpret complex security issues.
Conclusion: Recognizing and Countering Advanced Information Warfare
The patterns I observed are consistent with intelligence operations designed to protect extremist infiltration and Russian activities from legitimate investigation, as well as gather information from sensitive events and targets.
The individual presenting himself as “Grant Wescott”, who has been allegedly positively identified as American felon Gregory Richard Wolf, exemplifies evolution in information warfare that targets not just what we think, but how we think about threats.
For both security professionals and informed citizens, the case offers important lessons about recognizing advanced IO:
Be wary of individuals who claim expertise but lack verifiable credentials.
Watch for those who teach about threats while discouraging investigation of specific activities.
Pay attention to response patterns: professionals engage substantively with criticism, while operatives typically escalate to personal attacks when challenged.
Be particularly alert to content that manages your emotional responses to political figures or helps you process potentially threatening information in ways that maintain existing loyalties.
Advanced operations increasingly focus on protecting networks and managing information flows rather than simply promoting false narratives. Crucially, anyone engaging with independent voices claiming expertise in security matters should verify their backgrounds through multiple sources:
Check for professional credentials, look for verifiable employment history, and be suspicious of claims that cannot be independently confirmed.
Cross-reference their positions with established experts and be wary of those who discourage verification or respond defensively to reasonable scrutiny.
Be alert to inconsistencies of persona and narrative.
Trust your gut instincts while remaining appropriately skeptical. Advanced ops like these intend to become maximally effective by making targets doubt their own judgment and become dependent on alternative interpretive frameworks. Their ultimate goal is not necessarily to make you believe specific false information, but to compromise your ability to analyze threats independently.
Our democratic institutions depend on citizens’ ability to recognize and counter these threats. As information warfare evolves to target our analytical frameworks themselves, maintaining that capability becomes not just an individual responsibility, but a collective defense of democratic discourse.
By sharing these experiences and educating ourselves about evolving tactics, we can build resilience against even the most advanced attempts to manipulate our understanding of the world around us.
References:
[1] Cleave, Iona. “Elon will lose fight with Trump, Musk’s father tells Russia.” The Telegraph, June 9, 2025.
[2] Sauer, Pjotr. “Western guests including Elon Musk’s father to speak at pro-Putin oligarch’s Moscow forum.” The Guardian, June 9, 2025.
[3] Zadorozhnyy, Tim. “Elon Musk’s father to attend pro-Kremlin event in Russia hosted by far-right ideologue.” The Kyiv Independent, June 8, 2025.
About the Author:
Jackie Singh (@HackingButLegal) is a cybersecurity researcher and security analyst specializing in election security, foreign influence operations, and online extremism. Her public threat research work frequently makes her a target of the very actors she investigates who often attempt to manipulate her audience through defensive responses and counter-narrative injection. Singh’s current research focus relates to Russian influence networks and their operations targeting democratic institutions, particularly examining how hostile actors exploit social media platforms and construct false personas to manipulate public discourse.