These Texas Cops are Lying About Profiling Their App’s Users
…and Apple is laundering their lies right through the App Store.
Dear Reader,
There were several strange things about the tweet that landed in my DMs last week, not least of which was the attractive female police officer in heavy makeup, fully uniformed, geared up, and tastefully accessorized with earrings and an Apple Watch.
The weirdest thing about the tweet is that the police were promoting an app.
Cops sell apps now? I thought to myself.
The Precinct 4 Constable’s Office of Harris County, Texas describes itself as “the largest Constable’s Office in the United States”, and also has an unexpectedly popular Facebook page (and Instagram!) where they frequently post the mugshots of suspects, commentary alluding to local crime, and celebrations of successful operations.

In fact, they used the suspected terror attack in Brooklyn just this morning to promote this app as well.

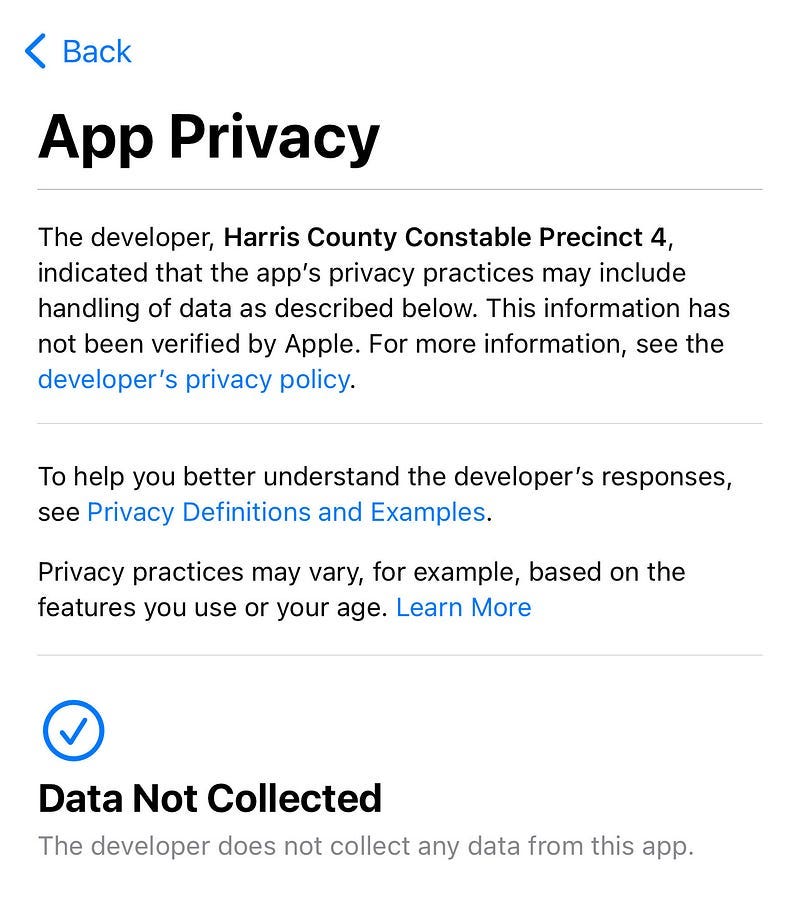
Anyway, I thought I’d download the app, “C4 NOW”, and check it out. Apple’s App Store told me they don’t collect any of my data, so it should be okay, right?
Let’s go! This won’t take long.
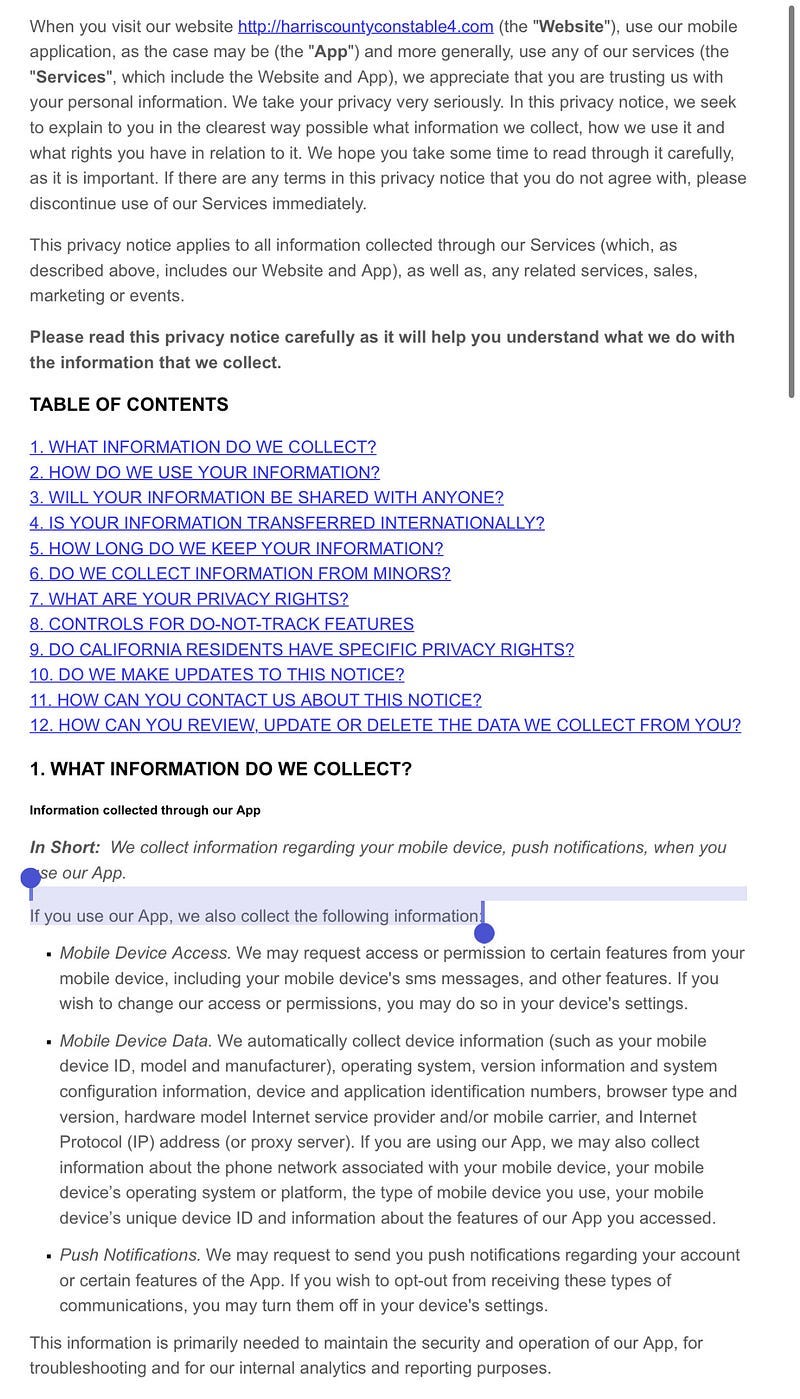
I clicked on “developer’s privacy policy”, where I was greeted with the following very contradictory information to what the developer had represented to Apple (highlighted emphasis mine):
So… while the developer (we’re talking about a police department here) represented to Apple there is no data collection occurring when we use their app, which Apple then repeated to me via their App Store, the developer’s own directly-linked privacy policy states (emphasis mine):
“Mobile Device Data. We automatically collect device information (such as your mobile device ID, model and manufacturer), operating system, version information and system configuration information, device and application identification numbers, browser type and version, hardware model Internet service provider and/or mobile carrier, and Internet Protocol (IP) address (or proxy server). If you are using our App, we may also collect information about the phone network associated with your mobile device, your mobile device’s operating system or platform, the type of mobile device you use, your mobile device’s unique device ID and information about the features of our App you accessed.”
So why did Apple allow these cops to lie?
Does Apple perform any verification of app privacy representations? Are apps scanned for any easily-identifiable marker(s) that would indicate a mismatch between a developer’s claims and their actual data collection practices?
Is their ecosystem actually as safe for privacy as we all think?
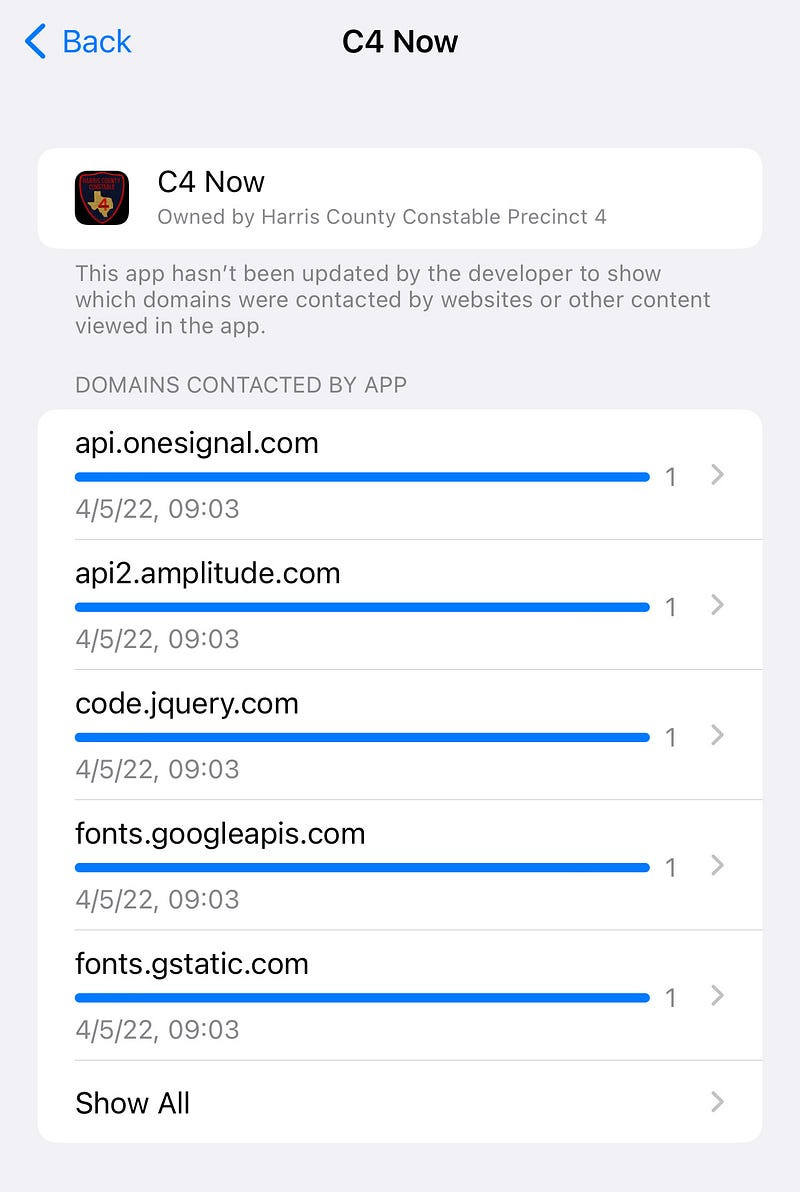
I wanted to verify the app was communicating in a way that indicated data collection was occurring, so I decided to enable iOS’s App Privacy Report (you can easily do this too).
I ran the app, clicked around a bit, and returned to the Report, which showed me the app had immediately made a request to Amplitude’s API.
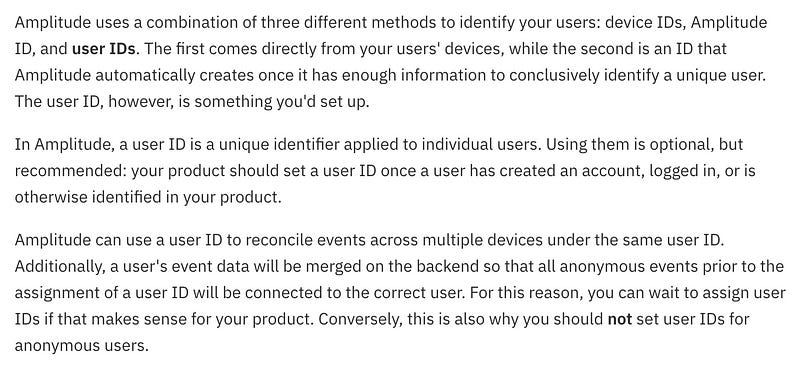
This API call ultimately indicates the developer implemented Amplitude’s SDK, which reports various data by default:
Their product allows for tracking of the specific behaviors exhibited and actions taken by users of the app across multiple devices, and creates a unique ID for each user of the App which cannot be changed.
Amplitude, as a behavioral tracking platform, doesn’t make it easy for developers who implement their SDK to stop collecting data from users on an existing project because that’s kind of the point of their product, and therefore an edge case.
Anyway, if the question is whether Apple actually limited the collection of our data by third parties by killing IDFA, the answer is “not really”.
Not to unfairly pick on Apple, since these types of apps also exist in the Google Play Store and likely have similar questionable data collection practices.
Beyond our basic individual right to privacy, isn’t holding law enforcement to a basic standard of integrity (per their own stated values) also something worthy of striving for?